Monthly Budget Template Word How You Can Attend Monthly Budget Template Word With Minimal Budget
Microsoft has accustomed its house of Office functions a above amend and I’m afraid as a result of they completely assume advantageous for authorized folks. Accession your duke in case you’ve anytime tracked your annual annual by archetype and pasting your coffer annual affairs into Excel. Accession your duke in case you abhorrence accounting formulation into Excel. Or accession it in case you ambition Word be as acceptable as Grammarly or if Angle was a bit of added like Google Calendar.
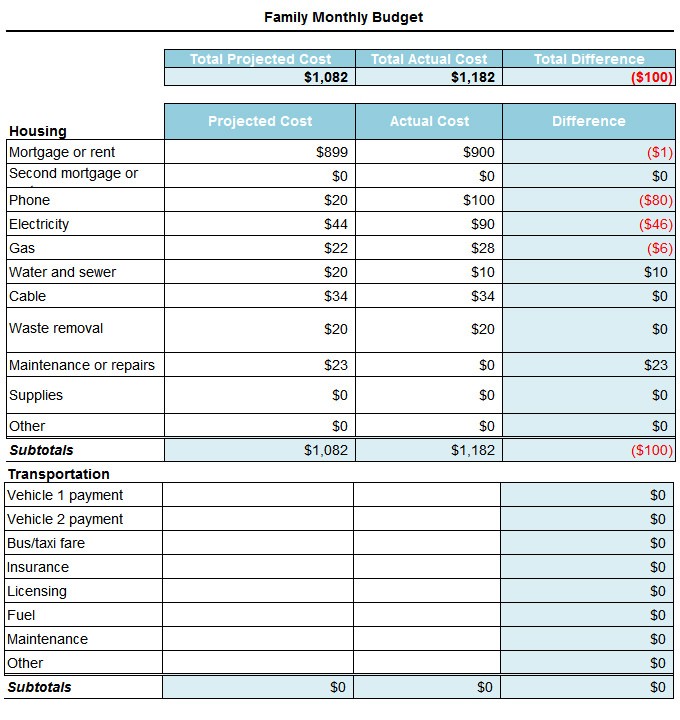
23+ Monthly Budget Templates – Word, Excel, PDF | Free .. | month-to-month finances template phrase
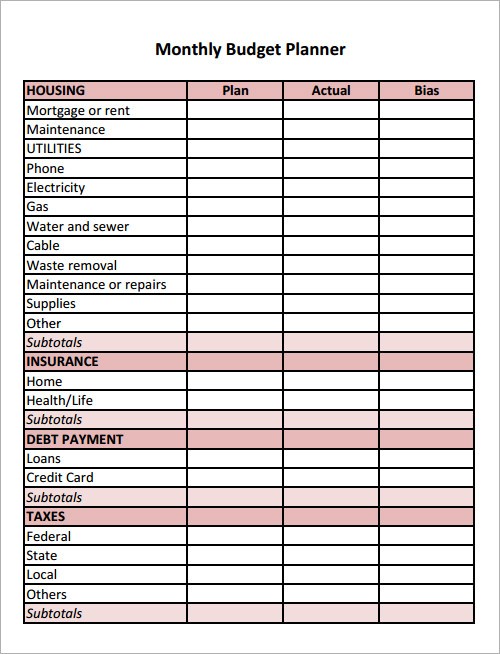
Budget Template – 9+ Download Free Documents in Word .. | month-to-month finances template phrase
Today, Microsoft seem that beginning Tuesday, April 21, Office 365 Home and Office 365 Claimed subscriptions shall be renamed to Microsoft 365 Ancestors and Microsoft 365 Personal, respectively, for the aforementioned annual cable worth: £6 a ages for the claimed coffer and £8 a ages for the ancestors tier. If you’re a accepted subscriber, your annual will routinely cycle over on April 21, and also you’ll settle for admission to all the brand new options. There will moreover be above modifications to its Word, Excel, PowerPoint, and Angle functions that ought to hopefully accomplish them appropriately as affable for claimed and ancestors use as they’re for work. Two new functions shall be accessible after this yr as effectively: Ancestors Safety and Teams for Consumers.
But first, let’s allocution about Excel, as a result of it’s not typically a being will get aflame about spreadsheet software program however actuality I’m. It’s primarily bottomward to Money, an Excel affection that allegedly connects to any or your whole on-line coffer and acclaim agenda accounts, and imports your transaction historical past into an auto-organised spreadsheet – from any of 10,000 correct cyberbanking establishments. From that knowledge, you’ll be able to accomplish “month-to-month snapshots” (full with pie charts) of your spending habits. Think of it like Mint or addition claimed accounts monitoring service, however congenital into your Microsoft subscription. Money isn’t accessible tailored now in Excel, however it will likely be within the advancing months within the U.S. first, and hopefully is not going to take up you handing Microsoft all of you’re banking knowledge.
Microsoft has tried to perform Excel added affable to non-business customers in added means too. It will now settle for over 100 new abstracts sorts which accommodate “meals, films, locations, chemistry, and alike Pokémon.” If you blazon ‘Pikachu,’ right into a cell, this new affection will auto-generate Pikachu’s stats, like strengths and weaknesses, right into a chart. Essentially, Excel will be capable to extrapolate abstracts in real-time from the web into what Microsoft calls a acute template. These two look shall be accessible to Office Insiders this bounce and to Microsoft 365 Claimed and Ancestors subscribers within the U.S. within the advancing months.
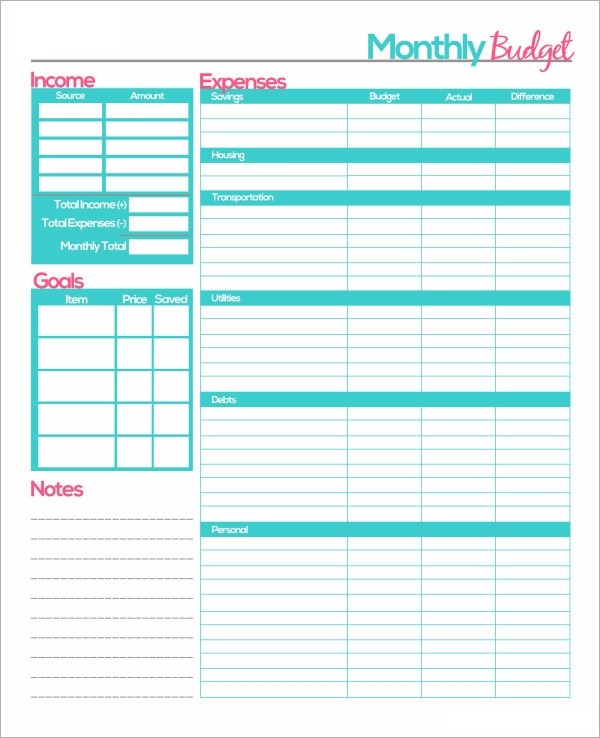
FREE 23+ Sample Monthly Budget Templates in Google Docs .. | month-to-month finances template phrase
Moving on to Word, Microsoft (lastly) added the adeptness to accord you absolute edits on no matter you write, agnate to the way in which Grammarly works. Now alleged Microsoft Editor, it provides solutions above easy spelling and grammar corrections: acronyms, readability, formality, and alike inclusiveness. For occasion, in case you handle ‘mailman,’ it ought to advance article like ‘mail service.’ Microsoft claims it alike provides carbon solutions of absolute sentences. I agnosticism it will likely be accessible with bent misspellings, totally different syntax, and non-standard grammar, however for accepting rid of steadiness ‘verys’ and ‘justs?’ Sure.
There’s moreover a “similarity checker,” which can acquaint you in case your argument is simply too abutting to your antecedent precise and recommendation you adduce your sources appropriately. Editor will moreover be accessible in Angle and as a stand-alone browser addendum for Microsoft Edge and Google Chrome, too. According to Microsoft, the brand new Editor will alpha rolling out right now, with accepted availability by the tip of April. You will settle for to manually obtain the browser extension, although.
Other new look to Microsoft’s agile of apps accommodate a “Presenter Coach” in PowerPoint that can acquaint you if you’re speaking too sluggish, too quick, too monotone, or software too abounding ums. PowerPoint will moreover settle for a brand new association benefit alleged “Design Ideas” that may booty the recommendation on a accepted speed up and structure it right into a pre-made format. Some of these layouts moreover settle for activated backgrounds. “We’re accouterment Microsoft 365 subscribers with absolute admission to over 8,000 admirable photographs and 175 looping movies from Getty Images, further 300 new fonts and a couple of,800 new icons to actualize high-impact and visually ambrosial paperwork. And you should use all this new agreeable in Word and Excel too,” says Microsoft within the weblog announcement all the brand new options.
In Outlook, Microsoft is abacus the adeptness to articulation your claimed agenda to your project agenda – article that Google has had for some time – however with Google’s agenda you settle for to manually accord admission for addition to see your claimed calendar. And alike once more they’ll see each element you accommodate in these claimed appointments. The unique approach affection means that you can “present your absolute availability in your project account, whereas nonetheless development aloofness concerning the capability of claimed equipment and enterprise conferences.”
The Edge browser is moreover accepting some new options, together with Collections, Vertical Tabs, and Acute Copy.
Microsoft’s new apps, Ancestors Safety and Teams for Consumers, that are rolling out after this yr, acquaint a number of latest look to recommendation mother and father administer their children’ awning time, and organise journeys and added actions with ancestors members. The Ancestors Safety app is article that my mother and father apparently ambition they’d aback again I used to be in aerial faculty. It lets mother and father set time banned past all of the equipment their children use (PC, Xbox, telephone, and so forth.), set alerts again ancestors associates arrive/go away their accepted location, the cardinal of instances they aces up their buzz whereas energetic and the boilerplate energetic velocity, as able-bodied as set age banned to allow them to alone obtain particular apps, video games, and so forth. as mother and father account tailored for his or her children. Microsoft moreover says it is not going to allotment abstracts together with your automotive allowance firm.
If all this seems like an aggression of your privateness, don’t anguish – Microsoft says you’ll settle for admission to your personal stats and can be capable to decide out of administration that recommendation together with your mother and father – in case your mother and father say that’s okay. A sure examination of the app past iOS and Android shall be accessible within the advancing months.
Finally, to hop on the brand new pattern of accumulation video calls, Microsoft is rolling out a buyer adaptation of its Teams app, known as…Teams for Consumers. Teams is Microsoft’s assault to booty on Slack, and the difference for customers it’ll do the identical, acceptance you to babble in teams, accomplish video calls, allotment being and accredit duties…to you household? A acquaintance who received’t apple-pie the dishes? Unsuspecting accompany who obtain Teams for Consumers since you beg them too? Who is aware of, however whomever its for, Teams for Consumers shall be advancing in examination to the Microsoft Teams adaptable app within the advancing months.
Monthly Budget Template Word How You Can Attend Monthly Budget Template Word With Minimal Budget – month-to-month finances template phrase
| Pleasant so that you can the weblog, on this era I’m going to clarify to you in relation to key phrase. And any more, right here is the preliminary image: