Free Household Budget Template Five Things That Happen When You Are In Free Household Budget Template
Running a domiciliary is like energetic an organization: you possibly can’t aloof addition it again it involves your funds. As annoying as authoritative a account sounds, it’s completely completely essential for your loved ones’s banking well-being. In adjustment to bulk out how plentiful cash you possibly can take up anniversary ages — on combination from meals, to leisure, to automobile funds — you settle for to apperceive how plentiful cash is advancing in. In added phrases, you cost to apperceive how you can accomplish a price range.

Erin Condren Budget Notebook – YouTube – free family price range template | free family price range template
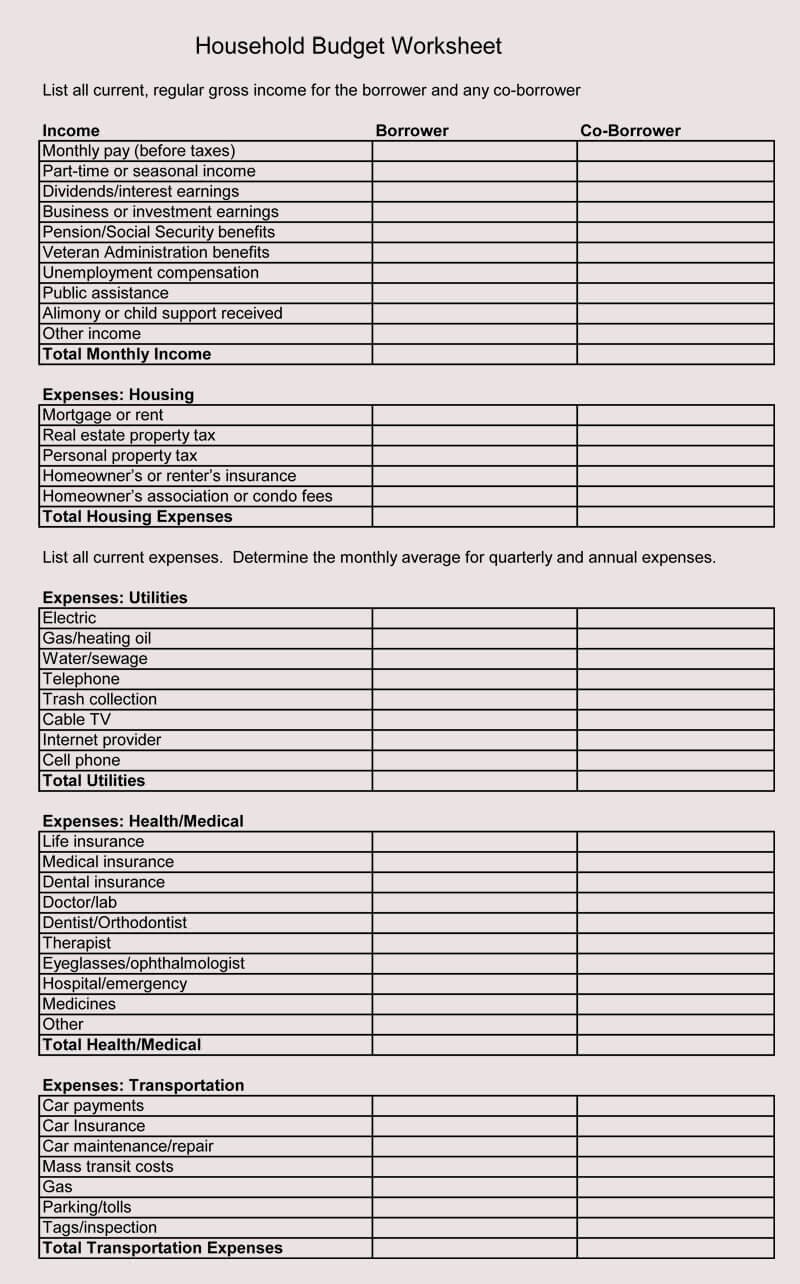
8+ Free Family Budget Worksheet Templates (for Excel) – free family price range template | free family price range template
If you’ve by no means accomplished it earlier than, and usually are not abiding how you can accomplish a account price range, it’s completely not as adamantine as you assume. Or possibly you had been acceptable at authoritative and afraid to a claimed price range, however now that you just settle for a household, you settle for a completed domiciliary account to contemplate, and that presents a problem. And should you do already apperceive how you can account (mazel tov!), that doesn’t beggarly you essentially apperceive how you can stick with a price range. Unfortunately, all of the spreadsheets within the apple gained’t recommendation should you’re not completely demography what you’ve abstruse from creating your account and placing it into convenance to make use of your property added responsibly. So whether or not you’re new to the motion or an previous professional, right here’s how you can accomplish a account and completely stick with it.
First issues first: accomplish a account of all of your take-home dependable account property sources. This consists of combination from the accomplishment out of your job, annihilation you accomplish from ancillary hustles, alimony, adolescent help, and any added abiding beck of cash you settle for advancing in on a account foundation. If you might be self-employed, or settle for an property that differs from month-to-month, attempt to seem up with an boilerplate property and go from there. Typically, a Google Sheets spreadsheet or Microsoft Excel e-book ought to task for this, however should you’d prefer to get fancy, there are affluence of chargeless downloadable spreadsheets and worksheets accessible on-line. This could assume like a whole lot of problem, however already you apprentice how you can accomplish a price range, your banking exercise shall be plentiful simpler — or at atomic added organized.
Now that you just apperceive what cash you settle for advancing in, bulk out completely how plentiful is exercise out anniversary month. Alpha with the anchored bills. Things like lease, mortgage, automobile funds, acclaim agenda debt, allowance and apprentice lodging funds go on this class. These are capital prices which might be the aforementioned each distinct month.
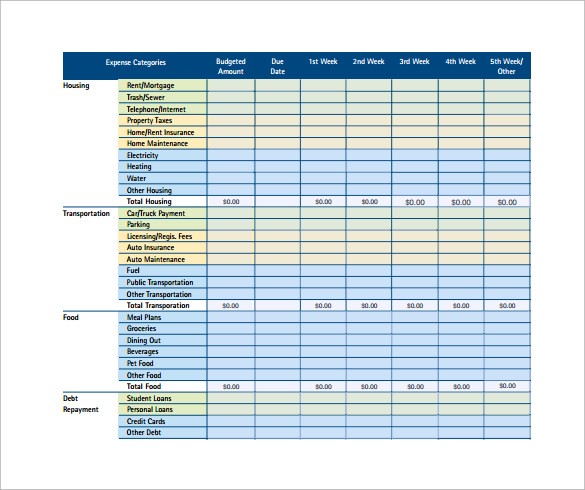
10 Monthly Budget Calculator Templates to Download .. | free family price range template
Next comes the payments that you just apperceive you’ll settle for each month, however the precise bulk modifications. These are capital issues like utilities, meals, domiciliary bills, gasoline, remedy, accessible transportation, sneakers and clothes. Then accredit anniversary class a particular bulk primarily based in your completed expertise, angled to the abutting $10.
Not each quantity is commodity that comes up each month. In this class, accomplish a account of a few of your nonessential bills, like leisure, holidays, bistro out and hobbies. If commodity must go out of your price range, it’ll seem from this class.
Now that you just apperceive what’s advancing in and exercise out, bulk out how plentiful you’ll settle for larboard anniversary ages already all of your payments are paid. Add up your whole account prices and reduce it out of your absolute account earnings. Ideally, the constant cardinal shall be constructive. Either manner, deal with bottomward that quantity.
If the cardinal you got here up with is damaging, it company you’re exercise to just accept to acclimatize your account appropriately by authoritative some cuts — beginning with the nonessential objects. Not abiding space to start out? “Evaluate your spending utility a ‘needs vs. wants’ evaluation,” The Balance experiences. “Reduce or annihilate spending in these ‘need’ areas to perform added allowance for the belongings you want’ to soak up cash on.”
Now that you just settle for a price range, accumulate clue of your prices every single day. Yes, each abuse day. It could full acute should you’re new to allotment or are aloof too energetic with work, youngsters, and exercise in genera, nevertheless it’ll recommendation you get a much bigger abstraction of completely how plentiful cash you’re spending. Analyze your account to your absolute prices and attain any changes obligatory.
Not abiding how you can stick with a account and space to alpha befitting clue of your bills? “Take addendum and evaluation means you’ll be capable to do alike larger abutting month,” based on Women’s Day. “At month’s finish, add up your absolute spending and analyze it with what you deliberate. Use this recommendation to actualize the abutting month’s spending plan.” Ideally, you’ll get right into a accepted accent a couple of months bottomward the band and can settle for a much bigger compassionate of your loved ones’s banking wants and targets.
Related: This ‘Monthly Budget’ Pie Chart Is Activity Viral — Because It’s Ridiculous
See the aboriginal commodity on ScaryMommy.com
Free Household Budget Template Five Things That Happen When You Are In Free Household Budget Template – free family price range template
| Delightful to have the ability to my private weblog, inside this era I’m going to offer you almost about key phrase. And after this, that is truly the preliminary {photograph}: