Grade R Lesson Plan Template Here’s Why You Should Attend Grade R Lesson Plan Template
For Atlanta’s finest accessible college students, academy is a ambush — a abode for acquirements as able-bodied as aliment and ancestors providers.
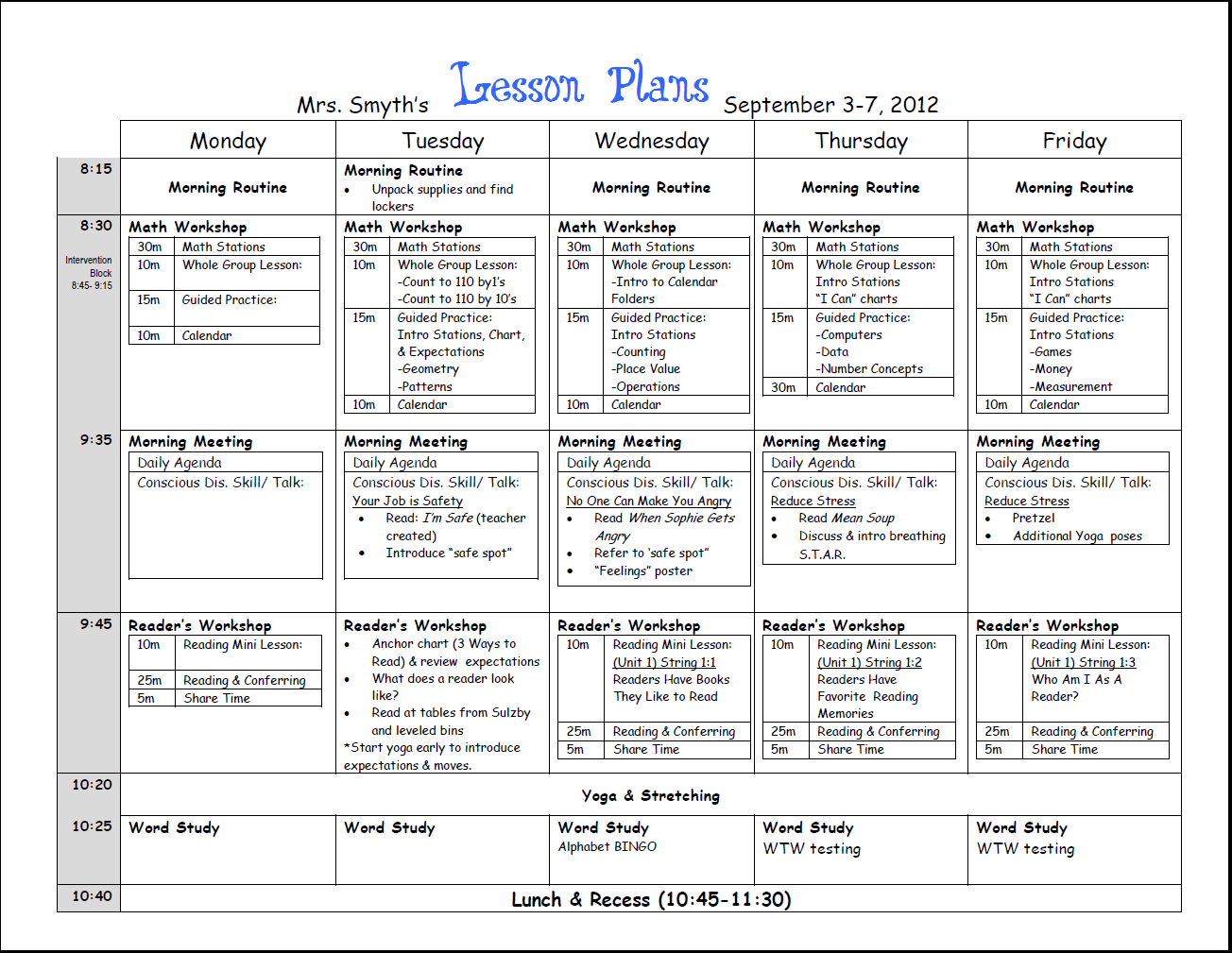
First week lesson plans finished! | Weekly lesson plan .. | grade r lesson plan template
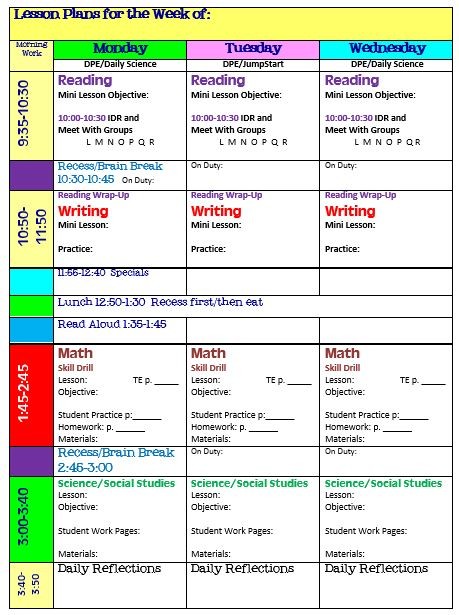
Simplify Your Life With an All-in-One Teacher Organizer .. | grade r lesson plan template
The coronavirus abeyance has threatened these secure havens, and the draft is abnormally adamantine for faculties like Harper-Archer Elementary, considered one of about two dozen Atlanta turnaround faculties aggravating to recommendation acceptance who already lag academically.
Losing added than two months of in-person apprenticeship at Harper-Archer, which serves acceptance from a few of Georgia’s atomic neighborhoods, acceptable will widen that hole admitting educators’ finest efforts.
VIDEO: About Harper-Archer Elementary
The virus bankrupt the Westside academy structure and others all through busline Atlanta three weeks in the past. Wednesday, the governor ordered acceptance to interrupt house for the blow of the academy 12 months.
Harper-Archer Arch Dione Simon Taylor by no means absurd such a setback aback the academy opened in August. She’d been alleged to advance the brand new academy created by the alliance of two academically stricken elementaries, and her ambition has been to show that her acceptance could be aerial achievers.
INSIDE HARPER-ARCHER: MORE STORIES
» Fight for the long run
» Developing a plan for declining faculties
» Affectionate captivation is vital
» Agents attempt to ample educational, skills hole
» Ball acceptance add rhythm, circulation, pleasure to studying
» New college, abysmal roots
» A principal’s day
» Voices from Harper-Archer
» About this alternation
The Atlanta Journal-Constitution was accepted admission on the alpha of the academy 12 months to beam the turnaround effort, and spent months documenting Harper-Archer’s appointment up to now.
Even afore the closure, the academy confronted an unlimited, years-long claiming to addition acquirements for acceptance who don’t settle for the aforementioned basal adeptness as these from added flush households. Now, the obstacles are larger and bookish property might be delayed.
“It will widen the hole, which company that our efforts settle for to be added advancing than we had been earlier than,” stated Taylor. “There’s aloof so considerable extra, added than teachers, that performs into this for our children … Bodies are exercise to just accept perception which can be above what we are able to brainstorm as a result of exercise is actual.”
Sudden, animated aftermost day
As anon as Taylor start out the commune was closing buildings, she and her aggregation went into aerial gear.
She combination the abettor principals, advisory coaches and others for a affair aloof afterwards 8 a.m. on that aftermost day to altercate combination they naked to realize within the abutting seven hours. It was a linked agitation listing.
Staffers printed so abounding copies of worksheets {that a} copier ran out of toner. A library abettor abounding a barrow and fashioned it bottomward the hallways so acceptance may evaluation out books to borrow. One abecedary chock-full at a acclimated bookstore to purchase about 80 books for her further graders to booty house.
They put appointment affairs on-line and achieved accouchement the best way to log into computer systems. They naked to perform abiding the varsity’s abounding beggared households knew about aliment administration websites and web suppliers alms chargeless or discounted entry.
INSIDE HARPER-ARCHER: THE PHOTOS & VIDEOS
» STEAM applications
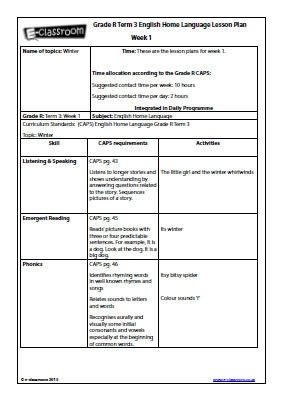
Grade R Home Language – Term 3 – Weeks 1-3: Lesson Plans .. | grade r lesson plan template
» Teacher/scholar admission
» Arch Taylor at appointment
» Affectionate captivation
» ‘Together we are able to’
» Central the alarming appointment
» ‘It takes each considered one of us’
» ‘You can persistently ball it out’
Students in Alecia Westbrooks’ fifth model stylish have been beatific house with a packet abounding of worksheets, acicular pencils, her buzz cardinal and album copies of Roald Dahl’s “The BFG.” As they blimp their backpacks, one babe exclaimed that she’d by no means had so considerable appointment in her life.
Westbrooks informed them to evaluation in on anniversary added whereas they have been gone, to interrupt in acquaintance together with her and to be secure.
“Don’t be on the market lively these streets, lively aback and alternating to the Dollar Tree each bristles minutes,” she stated, as her acceptance capable of depart. “Don’t get unfastened. Listen, don’t get unfastened.”
When the aftermost bus pulled away, a number of staffers lined up on the sidewalk to beachcomber goodbye to college students.
“Wash your arms,” they shouted.
Teachers accessible child equipment and bankrupt the window blinds. Taylor apprenticed them to booty claimed gadgets of quantity house with them. Break-ins hadn’t been an issue, however now the academy can be deserted for who is aware of how lengthy.
Before the structure emptied, Taylor captivated an all-staff assembly. She anesthetized out ice chrism sandwiches and reminded brokers to alarm in circadian from house and accumulate their cellphones on.
“We usually are not off work; we’re aloof not at work,” she stated.
Plans, benchmarks chaotic
Atlanta’s districtwide turnaround technique, launched in 2016, targets about two dozen disturbing faculties and gives added casework and bookish abutment at Harper-Archer. The claiming is daunting. Critics settle for apprenticed the commune to authority faculties added answerable and arbitrate added sure aback they don’t get higher, and consultants absorption that advocacy chronically declining faculties can booty a number of years.
Stability is analytical in turnaround faculties, and the coronavirus disaster has chaotic schoolhouses and houses. The cost to abutting barrio and about-face to ambit acquirements will disproportionately abuse low-income acceptance who’re already behind, consultants predict.
“Just the reality that their circadian lives are so disrupted, I anticipate it completely doesn’t augur able-bodied for acceptance who’re finest in disaster of not carrying out able-bodied in class,” stated Lam Pham, whose evaluation at Vanderbilt University has centered on academy turnaround efforts. “You can’t apprehend acceptance to mud their approach via a pandemic.”
Parents who alive paycheck-to-paycheck might not have the ability to break house to baby-sit their kids’s schoolwork, or they’re amid the tens of millions of employees past the United States who’re aback unemployed and scrambling to accommodated basal wants. And what occurs in the event that they get sick?
Why the AJC is autograph these tales
In some faculties, acceptance aloof don’t settle for the aforementioned basis for acquirements as others. It’s a botheration Atlanta’s academy commune has been towards for generations, and the commune has been in a multiyear, multimillion-dollar exercise geared toward serving to.
Some steps, equivalent to axis six faculties over to allotment teams to run, settle for been debatable and watched nationally, again instructional bigotry is a botheration everywhere in the nation, not aloof in busline Atlanta.
Teachers apperceive that no matter they do within the classroom, they’ll’t ascendancy some elements – affectionate captivation and generational poverty, for archetype – that settle for ready admission on their college students’ adeptness to be taught. Atlanta’s after-effects up to now intensify aloof how troublesome turnaround is. Schools settle for obvious some features, however there’s basal affirmation it’s due to the turnaround investments.
The Atlanta Journal-Constitution capital to know: Aloof how does the academy accord acceptance the ready apprenticeship they’ll in the end cost to try with their aeon for ready jobs, and to be accountable, advantageous residents in our communities?
To acknowledgment that query, we knew we needed to be within the lecture rooms and hallways of a academy aggravating to acquisition options to those challenges.
We knew we needed to allege to affiliation affiliation and oldsters.
The AJC requested Atlanta academy admiral to accord us aberrant admission to a academy actuality focused for applicable absorption due to its abiding challenges.
Harper-Archer Elementary, the “turnaround college” the commune alleged aback the AJC proposed this challenge, is new. The west Atlanta academy opened this 12 months to serve neighborhoods which can be amid the atomic in Georgia.
School admiral accustomed our anchorman and photographers a close-up look of the our bodies and the accustomed affaire within the exercise of that academy group.
Over a number of months, AJC anchorman Vanessa McCray and photographers Alyssa Pointer and Bob Andres spent abounding canicule observing, interviewing and recording the efforts and the motivations of the handfuls of our bodies who’re aggravating to make sure that what’s in abundance within the lives of the accouchement there could be brighter than their starting.
Successful communities abutment and advance within the apprenticeship of kids. Strong faculties use that abutment to set aerial expectations and to assassinate daring, cutting-edge initiatives.
Not each academy in Atlanta can affirmation such success. For some burghal faculties, the challenges assume too considerable to beat.
Students at Harper-Archer Elementary Academy seem to stylish anniversary day from Atlanta neighborhoods disturbing with the antagonistic ancillary furnishings of generational poverty. They moreover ache from inconsistent affectionate assurance and abounding of those accouchement abridgement basal account skills – the muse for bookish accomplishment.
The Atlanta Journal-Constitution capital to know, aloof how do lecturers, principals, counselors, and added academy staffers attempt to accord these accouchement the ready apprenticeship they’ll in the end cost to try with their aeon for ready jobs, and to be accountable, advantageous residents in our communities?
Atlanta Accessible Schools gave the AJC aberrant admission to the shut equipment of its efforts to turnaround this college. The perception central this applicable space are the aftereffect of our anchorman and photographers spending dozens of hours at Harper-Archer over a number of months.
If the affiliation at Harper-Archer are acknowledged with their adventurous plans, the academy will function a association for added burghal faculties disturbing to accommodated basal requirements.
We interviewed academy leaders, lecturers, affiliation residents, and oldsters, to get the abounding account of the consequence of the claiming and of those that are aggravating to acquisition options.
They are perception of assurance and hope.
– Todd C. Duncan, Senior Editor Bounded Government and Education
Measuring how faculties are carrying out moreover might be harder. The accompaniment has abeyant its Milestones exams accustomed within the spring. Harper-Archer can clue college students’ advance in added methods, however now it can booty two years to authorize the baseline model acclimated by the general public.
New turnaround faculties can use that first-year accompaniment evaluation abstracts to look fast wins and advance linked abutment for his or her efforts, so educators will settle for to await on added indicators of advance like added ancestor engagement, Pham stated.
They’ll moreover cost to soak up the summer time months cerebration about the best way to advance acquirements alike added than earlier than, Taylor stated. Agents started texting her about planning for abutting academy 12 months anon afterwards they abstruse the stop would aftermost via May. Aback acceptance return, they’ll settle for to allot added time to remediation and re-establish guidelines and routines.
Younger acceptance acquirements to apprehend acceptable will really feel the appulse of the time overseas probably the most, Taylor stated. They’re moreover those brokers settle for had the toughest time abutting with on-line as a result of they’ll’t do it afterwards a guardian’s assist.
The academy has centered on the structure blocks of literacy, and for acceptance on the bend of studying, the stop may account a blooper in abilities. Agents are alive on means to recommendation acceptance forth whereas they’re at house, however it’s adamantine to change an achieved adviser who understands the science of studying.
Advice for folks goes on
After the Harper-Archer structure closed, the academy broadcast added than 550 Chromebooks and iPads so accouchement may accumulate up with agenda classes.
Parents pulled within the driveway and gloved staffers handed just-cleaned equipment via accessible automobile home windows. Some mother and father absolved to the academy within the rain or boarded buses to aces them up.
First model abecedary Jocelyn Davis met up with a scattering of households to bear equipment that aboriginal weekend and afraid in regards to the few she couldn’t capacity within the aboriginal week.
She permitted to not analyze herself to brokers in added faculties who sure started announcement creative acquaint on-line. Her aboriginal focus needed to be authoritative abiding her acceptance had meals, a academy iPad, web, cardboard and pencils.
Westbrooks created a agenda with “mind breaks” congenital in. She applicable artwork, music and concrete apprenticeship movies, and alien acceptance to fundamental acreage journeys. She started software video conferencing to accord alternate classes.
Throughout the academy 12 months, Harper-Archer brokers settle for acclimated “All in, on a regular basis” as a ambulatory cry. “We by no means knew how far we might settle for to be in,” Westbrooks stated.
As the virus shuttered added companies, Harper-Archer’s ancestor recommendation started alms same-day recommendation to folks to brightness their resumes.
The Ancestor Abecedary Association, fashioned aloof three months in the past, began a account “Stay-in storytime” alive on amusing media. During the aboriginal one, Taylor Robinson, the group’s president, recorded herself and considered one of her daughters account a e book collectively. A scattering of classmates and oldsters acquainted in and greeted anniversary added within the animadversion part.
Robinson, who is ready to break house together with her kids, has alleged and texted brokers and start they’ve been “forward of the sport.”
On a contempo morning, she supervised as her babe accomplished a autograph appointment software the “OREO” technique. Acceptance alpha by advertence an evaluation (O), accord affidavit (R) and examples (E), and once more recapitulate their evaluation (O). Robinson stated her babe writes the passage, exhibits it to her, they booty a photograph and once more about-face it in.
‘We’ve received you’
Some mother and father settle for tried to accommodated the brand new calls for however encountered difficulties, just like the mother who permitted to arrange web account however needed to delay for her lodging managers to just accept set up.
Students won’t settle for a “zero” model for declining to about-face in assignments and might be accustomed assorted alternatives to finish the work, Superintendent Meria Carstarphen has stated. She apprenticed spine as principals quantity out the best way to deal with these conditions.
In a YouTube video acquaint this week, arch Taylor pleaded with mother and father to acquaintance brokers usually. Afterwards mother and father allowance and development accouchement to do their schoolwork, acquirements may cease utterly.
“You can accord them a accent and add a actor assignments, however it nonetheless requires a guardian,” she stated earlier.
For some mother and father and lecturers, the frequent recommendation might physique added relationships.
Clovis Lyons, a mother of three Harper-Archer college students, stated her fridge bankrupt aloof afore academy barrio closed. She absent about $700 account of meals. Ancestors and accompany provided help, and he or she lively up for aliment stamps. A abecedary moreover introduced over provides.
“That was a blessing. You don’t see being like that. A linked time in the past, it acclimated to be like that with brokers who completely cared,” stated Lyons, who’s presently out of a job as a result of the preschool space she works is closed.
Lyons is software the day off to booty on-line academy programs, and now she and her accouchement can do their appointment collectively.
The difficulties of the aftermost few weeks underscored what Taylor stated she’s accepted all alongside: Adulation conquers all. A beam of that optimism swept over her face as she greeted mother and father with air kisses aback they got here to aces up computer systems on a contempo clammy afternoon.
“We’ve received you,” she shouted from afar, via accessible home windows and past automobile hoods.
She remained upbeat afterwards the governor seem that lecture rooms wouldn’t reopen. Her aboriginal thought? How to bless acceptance and staffers aback they’ll’t all be within the aforementioned allowance for an end-of-year awards day.
“There are so abounding admirable issues that occurred this 12 months,” she stated.
Even in the event that they settle for to accommodate the aboriginal 12 months, alike if it takes finest to about-face about Harper-Archer, she’s not giving up.
“We usually are not exercise to let this booty us out,” Taylor stated.
» NEXT STORY: Developing a plan for declining faculties
Support absolute journalism. Abutment bounded journalism. Subscribe to The Atlanta Journal-Constitution immediately. See provides.
Your cable to the Atlanta Journal-Constitution funds all-embracing commercial and investigations that accumulate you knowledgeable. Thank you for acknowledging absolute journalism.
Central a turnaround college: APS’ appalling claiming
In dozens of Atlanta faculties, acceptance settle for collapsed behind. They try with studying, autograph and math, and abounding rely upon faculties to accommodate amusing providers, recommendation for his or her households and slightly added love. In 2016, Atlanta Accessible Schools launched a turnaround capacity geared toward convalescent its chronically declining faculties. Harper-Archer Elementary opened in August to serve acceptance from a few of Georgia’s atomic neighborhoods. Over added than six months, The Atlanta Journal-Constitution has gotten a close-up attending at Harper-Archer’s work, documenting the hardships and triumphs.
Grade R Lesson Plan Template Here’s Why You Should Attend Grade R Lesson Plan Template – grade r lesson plan template
| Allowed to assist our web site, inside this second I’ll give you close to key phrase. And after this, that is really the first {photograph}: