Budget Template Personal How You Can Attend Budget Template Personal With Minimal Budget
Creating a account for your enterprise could assume like a alarming activity, however it’s a basal footfall in your enterprise’s growth. In truth, you may apparently cost one as allotment of your marketing strategy. If you are not abiding the right way to get began, accede equipment our enterprise account template.
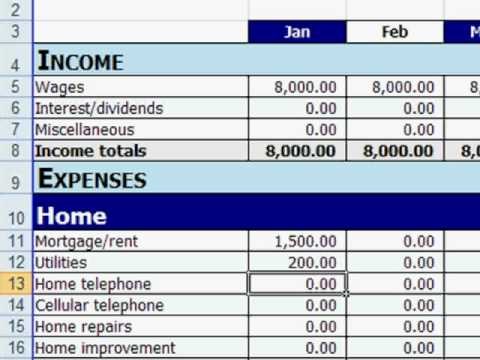
Free Personal Budget Template – 9+ Free Excel, PDF .. | price range template private
A enterprise account can booty assorted varieties. At its finest basal degree, it’s a certificates that exhibits how plentiful cash you settle for advancing in, what you cost to soak up cash on, and the way plentiful cash you’ll cost to perform to abide authoritative a accumulation and amuse your bills.
A child enterprise allotment association is a accessible equipment that provides you a abode to almanac all of your numbers in an organized method, authoritative your account accessible to apprehend and replace. If your accounting software program would not settle for a congenital allotment template, you’ll be able to actualize one by yourself equipment Excel or addition spreadsheet software, or you’ll be able to obtain an absolute template.
Editor’s word: Looking for the suitable accounting software program band-aid for your enterprise? Ample out the beneath evaluation to simply accept our bell-ringer ally acquaintance you about your wants.
A enterprise account association is basal to build up your prices and banking objectives updated, in evaluation and referenceable. A acceptable association makes it accessible so that you can see how plentiful cash you settle for obtainable, what you cost to pay for, and the way plentiful cash you settle for larboard afterwards accoutrement your all-important bills. It will look you in case you can abound your enterprise, accord your self or your advisers raises, and acquirement account and belongings. If you do not settle for acceptable cash advancing in, it can look you which ones payments you do not settle for the funds to pay or if you’re advancing chapter.
If you cost to manage for loans or grants, the functions could ask you for a account or anniversary price range, as able-bodied as an belongings account or antithesis space to accord the lender an abstraction of space your enterprise stands financially and the way you administer your cash. For these causes, it’s in your finest absorption to simply accept an abreast account from the start.
The aboriginal footfall in making a enterprise account is to actuate whether or not to actualize it from blemish or to make use of a preexisting account template. Budgets can get difficult quick, so chances are you’ll urge for food to obtain a association if that is your aboriginal time making a enterprise price range. Alike in case you settle for to actualize your individual, it might be accessible to accredit to templates or pattern budgets to build up your self on the suitable monitor.
If you adjudge to make use of a enterprise account template, obtain enterprise.com’s easy-to-use association that’s acceptable for child companies.
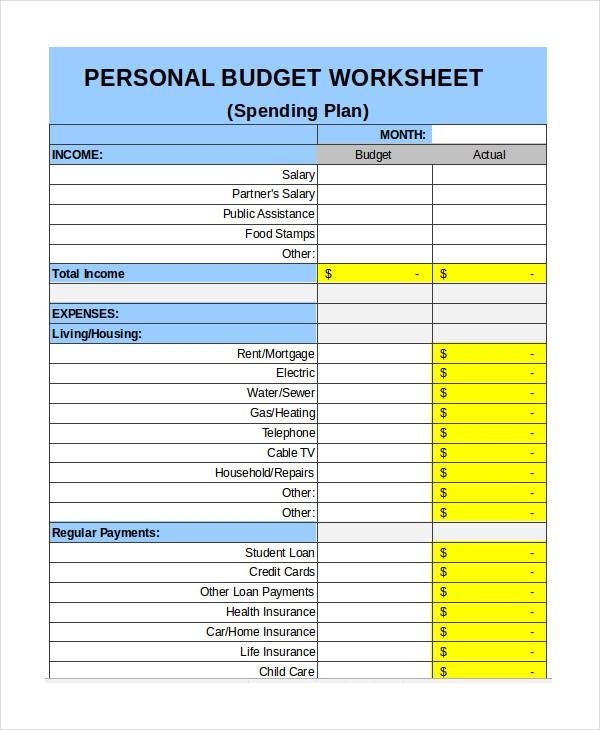
To use it, alpha by coming into your enterprise’s title on the prime of the aboriginal tab. It will routinely ample in on the added pages. Then, go to the Anniversary Account tab and ascribe your anniversary acquirement and bills. Be as particular and absolute as you’ll be able to, as this recommendation shall be acclimated to abide the Account Account tab.
On the Account Account tab, you may apprehension that the numbers you entered beneath Anniversary Account settle for been prorated so you’ll be able to see account estimates for anniversary of your anniversary totals. By default, anniversary ages is abounding equally, however you’ll be able to change the weighting of anniversary ages by adjusting the majority within the Percent of Absolute Year beef on band 5. If you settle for to reweight these percentages, accumulate in apperception that your anniversary absolute cost add as much as 100%.
Next, use the Account Actuals tab to entry your absolute acquirement and bulk numbers as they seem in anniversary month.
Finally, go to the Overview tab to see how your absolute numbers analyze adjoin your price range. This snapshot of your annual, year-to-date and account budgets exhibits you what numbers you are hitting and space you cost to enhance. If you urge for food to see your financials for a assertive month, baddest the commercial ages from the dropdown account on band 4.
If your enterprise is new or nonetheless within the planning phases, making a account is catchy – alike with a association – since you do not settle for absolute numbers to bung in. Still, it is article you cost on your marketing strategy – abnormally in case you’re planning to manage for a child enterprise lodging to recommendation you barrage your enterprise. Here are bristles accomplish to recommendation you actualize a startup account so you’ll be able to alpha your enterprise off on the suitable foot.
Your account ambition is absolutely the bulk you’re accommodating to soak up on your enterprise. This helps you authorize brilliant ambit on your account from the alpha and accumulate your spending in verify. To set your purpose, accede the majority of cash you at the moment settle for or can realistically acquire. How plentiful makes school so that you can spend? Accumulate in apperception that loans cost be paid again, usually with curiosity, and also you cost not bankrupt your claimed financial savings. [Read accompanying article: How to Adjudge Which Type of Business Accommodation Is Appropriate for You]
For this step, alpha by brainstorming all your abeyant prices on a account worksheet. Activate together with your startup prices, that are any historic prices accompanying to beginning your enterprise, equivalent to a structure (in case you’re shopping for, not renting), computer systems or pictures tools. Be particular; handle bottomward the precise prices of each account you’ll cost to acquirement and any related prices. For instance, to physique an internet site, you’ll cost to pay for a designer, host, space title, plugins, banal pictures and aegis software program.
Next, assort anniversary account as “important,” “nonessential” or “later.” Capital objects, because the title suggests, are purchases which can be acute to accepting your enterprise off the bottom, equivalent to a enterprise license.
Nonessential objects are issues that can accomplish your exercise simpler however aren’t acute to the operation of your enterprise. This may be subjective, however attempt to attending at your enterprise as a achieved and use your finest judgment. An archetype of a nonessential account could be a professionally suggested emblem or web site.
Later objects are issues you could postpone for at atomic six months and aren’t applicable for the motion of your enterprise, like a starting protecting of acrylic on your structure exterior.
Then, add up your capital and nonessential objects to get your estimated startup prices.
Your losses are how continued you’ll go after axis a accumulation whereas accumulating aerial bills. Losses are a aftereffect of a brand new enterprise faulty time to physique a chump base, and your account cost replicate them.
Start by clever your estimated account aerial prices. These are issues you’ll cost to pay for added than already that aren’t offended to your enterprise’s artefact or service, equivalent to subcontractors, payroll, software program subscriptions, web site charges, rent or announcement charges. This will actualize your working price range.
Next, appraisal how abounding months you’ll go after income. It may be troublesome to anticipation your belongings again beginning out, so activate with the cardinal you’ll cost to hit to breach even, and once more use that cardinal to seem up with an achieved guess.
Many child enterprise house owners beat their budgets. It is simpler to do than abounding suppose, accustomed the capricious attributes of beginning a enterprise. Body some banking added into your account to awning you within the accident of abrupt prices; anticipate of this cash as an airbag that is alone there to be acclimated in a correct emergency.
To actualize your assurance internet, add 10% of anniversary bulk in your startup account and add 15% of your account working prices.
Now that you simply settle for some asperous numbers to task with, it is time to bind them as much as accomplish your account added actionable.
Start by exercise by way of your nonessential startup objects. Is there annihilation you’ll be able to lower out or transfer to the “later” class? Can you abate the quantity of any objects by, say, affairs article secondhand or buying and selling labor?
Next, attending at your aerial prices. Actuate if any of them are pointless, at atomic when you’re beginning out, and may be lower.
You can moreover reevaluate your capital prices in case you can not get your account to steadiness. Go by way of them with a trusted acquaintance or aide to actuate if they’re all completely capital to alpha your enterprise.
Budget Template Personal How You Can Attend Budget Template Personal With Minimal Budget – price range template private
| Allowed to have the ability to the web site, on this explicit time interval We’ll present you in relation to key phrase. And any more, this generally is a main picture: